Top 10 Skills Required to Become a Pro-Hacker
The term hacker literally means a person who uses computers in order to get unauthorized access to data. Hacking is not crime unless and until you do it to get unauthorized access. In this article, you will see the skills required to become a pro-hacker. Stealing data and hacking into networks are not the only things that hacker does. The skills mentioned below can also help you to tackle with hackers who do hacking to obtain unauthorized access data.
Contents: [show]
Top 10 Skills Required to Become a Pro-Hacker
#1 Basic Computer Skills

You may laugh at this skill. However, it is very necessary for a hacker to get a firm hold on the functioning of the computer. Also, you must be able to use the command line in Windows and editing the registry and setting own networking parameters.
Also Visit: Become Ethical Hacker, Get our courses now#2 Networking Skills

The skills mentioned below will be helpful for those persons wishing to become hackers as these skills will help them to understand about its functioning.
DHCP, NAT, Subnetting, IPv4, IPv6, Public v Private IP, DNS, Routers and switches, VLANs, OSI model, MAC addressing, ARP. To Learn “Networking”, visit this link.
#3 Linux Skills

No Doubt, Linux is the most favorite operating system of hackers. Almost all the tools that we use as being a hacker are developed for Linux. It has more potential that hacker requires but are not available on Windows. That’s why hacker prefers to use Linux Operating System. You can learn Linux skills by visiting this link.
#4 Wireshark
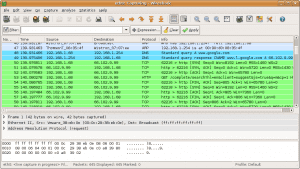
Wireshark is open source packet analyzer and available for free. It is particularly used for network troubleshooting, analysis, software and communications protocol development as well as in Education.
#5 Virtualization

It means the making of the virtual version of something like operating system, server, storage device or network resources. It helps in testing the hack that is going to take place before making your hack go live and it also helps to check and revise the hacks before making it go live.
#6 Security Concepts

It is also vital skill to understand security concepts as well as technologies. A person having a strong hold on the security can control the barriers set by security administrators. It is also important for a hacker to learn skills like Public Key Infrastructure (PKI), Secure Sockets Layer (SSL), Intrusion Detection System (IDS), Firewalls and more. If you are a learner in hacking, you can get most of these skills in a security course like Security +. Become security expert by visiting this link.
#7 Wireless Technologies

Wireless Technology means the procedure of sending information via invisible waves in the air. Persons who wish to hack wireless devices must first understand the functioning of it. So you must learn encryption algorithms like WEP, WPA, WPA2, the four-way handshake and WPS. Moreover, you can also learn and understand things like protocol for connection and authentication as well as restrictions on wireless technologies.
#8 Scripting
It is considered as an important skill to become a pro-hacker because if any hacker is using tools of another hacker, he/she will be dis-rated for using them. Also, security administrators are vigilant about the hacking attempt, and they come with a new tool to cope with hackers.
#9 Database

A database is a structured set of data present in computer and which is accessible in numerous ways. For those hacker’s who wish to hack the database, then it is necessary for them to understand the functioning of the databases. It consists of SQL Language. It is better to know the big DBMS like Oracle, MySQL or Oracle.
#10 Web Applications

Web Applications is software which you use on the Internet via your Web Browser. It has been witnessed that web applications have also become a prime target of the hackers since the last few years. You will be victorious for your task if you understand the functioning of web applications and the databases backing them. Moreover it will also help you to make your own website for the purpose of phishing or other. Learn these languages by visiting this link.
We just highlighted some skills that are necessary to become a pro-hacker; several other skills can make you pro-hacker too. If you have something more to add, you are welcomed in the comment section below.
Owner Info-:
-rishi
E-mail : rishivaishnav2019@gmail.com
Instagram : @rishi.__________
THANKS FOR VISITING
-rishi
E-mail : rishivaishnav2019@gmail.com
Instagram : @rishi.__________
THANKS FOR VISITING

Comments
Post a Comment